Net Scavenging
Current state: Open to the public.

Getting started
Step 1: Register and login in Dark City.
Step 2: Open your inventory with the command inv and activate your Biometric Scanner or bioscan. If you still don’t have one, you may acquire one here.
Note: If you own a Burner Scan, follow the exact same process. Your Burner Scan will be valid as a bioscan for 15 days. You can consult the expiry of your Burner Scan using the command profile in the terminal.
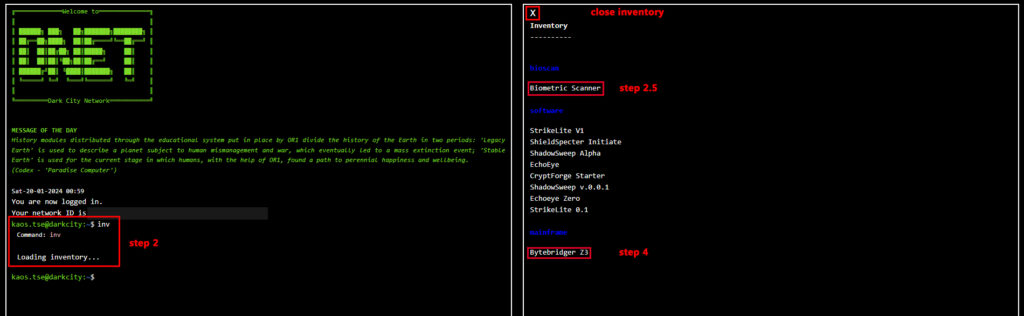
Step 3: After activating your bioscan, close the inventory and open it again to refresh it and receive any new items allotted to you. OGs and a group of early players will earn a free software starter pack and a beta version mainframe. Subsequently, software and other hardware will be available in the Dark Market.
Step 4: Select your mainframe, activate it and then select the option to “manage” it.
Step 5: Select software from your inventory and activate them in your mainframe management screen.
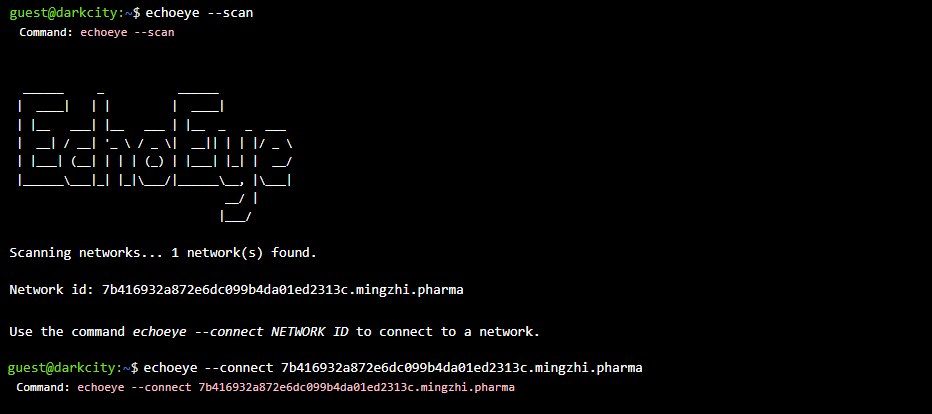
Step 6: Use the “Echoeye” software in the terminal to scan and connect to networks. Use the following commands:
echoeye --scan will search for available nodes in the vicinity. If you´re not connected to any server, Echoeye will try to find any connectable servers. This command only unveils networks of Level 1.
echoeye --connect NETWORK_ADDRESS will connect you to the outtermost node of a network server and let you – or your finds – to start the invasion. These addresses are stable, they can be shared with other hackers if needed. For example: echoeye --connect test.darkcity.beta
Note: You spend “battery” stats everytime you execute the Echoeye software.
Objective
The objective of Net Scavengers is to ultimately breach networks and get rewards.
Players start invading Level 1 networks . Once they breach the last node of a level 1 network, information about a Level 2 network will become available for download.
By invading networks, players earn XP points to level up their characters, as well as Notoriety points with which they will be able to earn $NOR Runes.
Tips
- Read carefully the manual and understand the rules.
- You won’t be able to make it alone, you will need to form groups (in your gang or elsewhere) to gather players to attack the same network simultaneously.
- Network addresses are scarce and valuable information (in special those of networks above Level 1), so beware with whom, when and under which conditions you share them.
- Items do make a difference in your performance. Get your Avatar and keep an eye on the Dark Market to make sure you are not missing anything!
- Your alliances with players and groups matter. This is a social game.
- Use the marketplace to find items that will enhance your performance.
- Adjust your browser zoom if needed by using the keyboard Control Key with the “+” or “-“ keys, or Control Key + Mouse scroll wheel.
Rules
You need to connect to networks, interact with the nodes within and breach them until you breach their last, most powerful node (security level: “Ultra”). Then you will be able to connect to a higher level network .
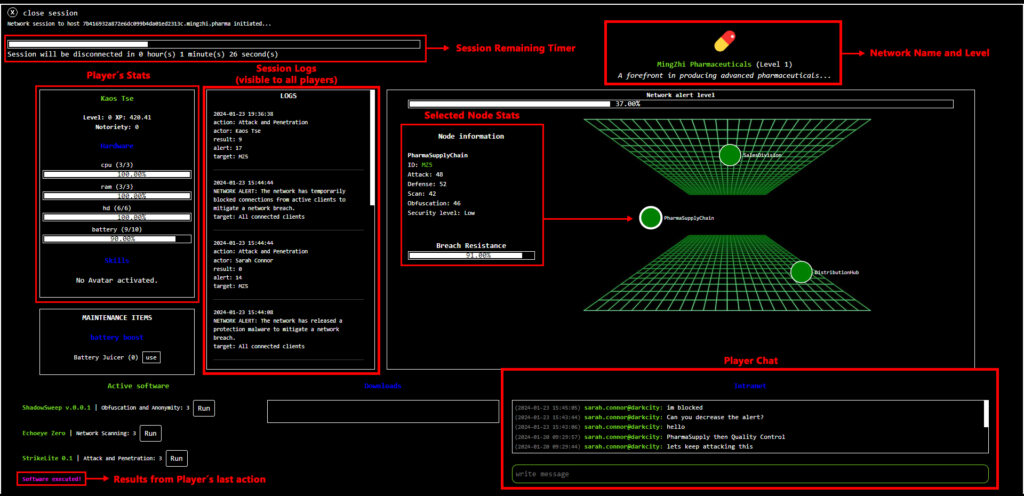
Network Connection Time
How it Works: Once connected to a network, players have 2 minutes to interact with it. After the session timer expires, players can’t interact anymore, and their visibility and any downloadable data packages are reset. For every interaction with the network during the session, the player performing the action gains 20 extra seconds of session time. An interaction means executing any software against one of the nodes of the network.
Using software
Once connected to a network, you will be able to use the active software in your mainframe. The starter pack comes with 3 softwares:
- ShadowSweep: Use it to decrease the Network Alert of a network.
- EchoEye: Use it to gain visibility over the node structure of a network.
- StrikeLite: Use it to attack a node and decrease its Breach Resistance.
- CryptForge: Decryption software used to open downloaded files.
Either run the appropriate command syntax at the terminal prompt or select a node in a network and “run” your software!
Stats
Hardware stats
- CPU: The ability of players to execute software properly. 100% of CPU means players execute software at their maximum capacity. Example: if your CPU is at 50%, you are executing software at half of its capacity.
- RAM: How many softwares can be active at the same time in the mainframe of a user.
- HD: How many softwares a user can store in their inventory.
- Battery: Defines the ability to execute software. Once the battery reaches zero, a user is not able to execute software.
You can consult your stats in real time once you connect to a network. If you are in the terminal, type stats to check them.
Physical stats
Not activated during Season 1: Net Scavengers.
Avatars
Avatars provide extra skill bonus(es) to players once activated and can drastically enhance in game performance. Activate your Avatar in your Inventory window, by entering the command inv in the terminal.
Recovery
- Players: Recover all their stats in full every 6 hours. Every 30 minutes, they recover partially their stats.
- Networks: Recover every 45 minutes. Their level and nature determine how much. While recovering, a network may recuperate Breach Resistance of their nodes, remove blocklists, and decrease their Alert Level.
Maintenance items
Players can acquire items in the Dark Market to temporarily boost their stats while attacking a network. Each item has a specific cool-down period after usage.
There are two main maintenance items in Season 1:
Battery Juicer
A gadget temporarily plugged to the mainframe, used to recover battery points.

You can acquire one at the Dark Market.
A Battery Juicer can be used once every 3 hours. The Battery Juicer 500 recharges 5 battery points.
How to use it? You can use it through the stats interface (type command stats) or during a network attack in the section “Maintenance items”.
Thermal Paste

This disposable gadget counters malware installed by networks, recovering CPU.
IMPORTANT: Maintenance items are disposable, usable items and can't be minted. Players spend the respective item in every usage.
Networks
Network Types: There are Networks of 5 different levels. The higher the level, the higher the stats of the network nodes and the better the loot gained by breaching them.
Nodes in a Network: Players attack networks by using software against one of their nodes. Users can only target “Low” security level nodes or the ones connected to a previously breached node.
Node Types: A network has 4 different node types according to their security level: Low, Medium, High, and Ultra. The higher the security level, the more difficult it is to breach the node, and better loot is gained by breaching them.
Nodes’ colours and their security level (difficulty)
Low security
Medium Security
High Security
Ultra Security
Breach Resistance
How it Works: Nodes start with full Breach Resistance, 100%. For every successful attack executed against that node by a player, the Breach Resistance decreases. A node is “breached” once its Breach Resistance reaches 0%. Loot download becomes available to those participating in the network session, and all the nodes connected to the breached node can now be attacked as well.
Network visibility
From the start, you will only be able to see “Low” security level nodes within a network. You can use the Echoeye software to increase your visibility and find the easier path to the last node of the network.
Also, once a node is “breached”, the network visibility increases automatically – and so does the Alarm.
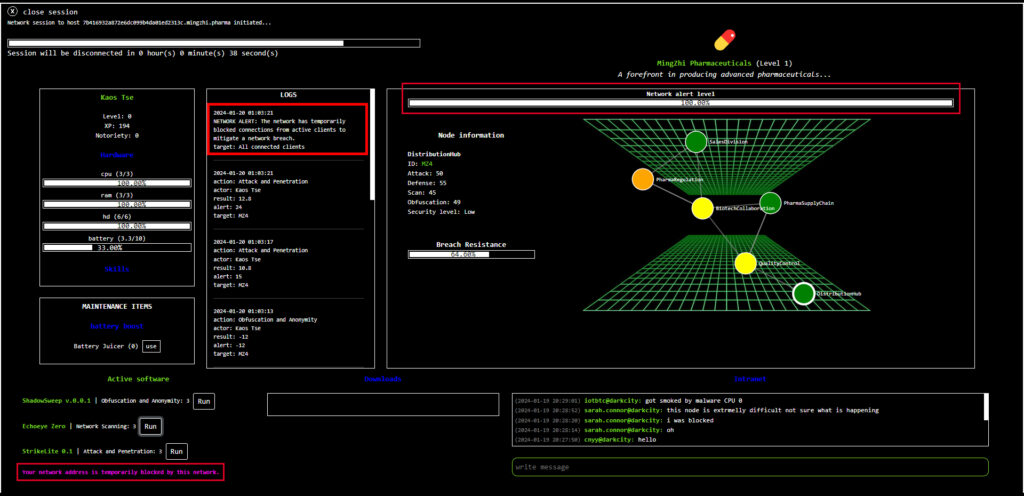
Network Alert
How it Works: For every interaction with a node in a network, the Alert Level of the whole network increases. Executing “Obfuscation and Anonymity” software, like ShadowSweep for example, against a node in the network decreases the Alert Level of the network.
Network Reactions: Once a network reaches 100% Alert Level, it starts to respond negatively to any interaction with it. Network responses in this case can be:
- Blocking connections of users to the network, meaning users cannot interact with the network during a certain period of time.
- Installing malware on users connected to the network, decreasing CPU capacity of players.
All players connected to the network are affected by the network response when its Alert Level gets to 100%, regardless of which player performed the interaction.
Where is the next network to invade?
Once the last node of a network is breached, a data package will become available for download to all users connected to the network session, containing crucial information about other networks. The users need to download this data package and decrypt it later in order to access this information.
Logs
Every interaction with and from the network is stored in the Logs window. Players are able to access the last 10 log entries.
Data Packages (Loot)
How it Works: Once a node in a network is breached (Breach Resistance reaches 0%), data packages become available for download to those connected in the network. Players can only download data packages once from each node. While downloading data packages, players cannot interact with the network.
NOTE: Players need to click on the button "Download" to download the data package. This should be done while the network session is still connected. If you don't download the package, it won't show in your files later and you will need to invade the network again to have another opportunity to download it. After download, you can decrypt your data packages at anytime.
Loot Types: Data packages may contain the following.
- $DRK prizes
- Crucial information for the gameplay (for example, new network addresses to more powerful networks)
- Pieces of software and hardware blueprints (useful to craft exclusive, new software and hardware in the future)
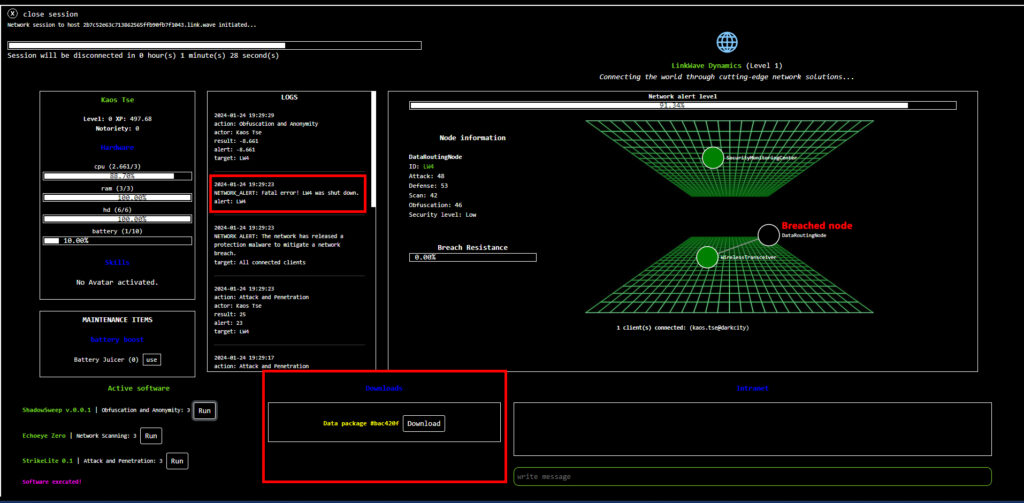
Accessing and decrypting data packages
Data packages need to be decrypted with specific software.
- In your Inventory, activate a decryption software in your mainframe. Type
inv, then select your mainframe and click on “Manage”. The CryptForge Starter is an example of a decryption software. - Enter the command
filesin the terminal, then choose the data package you want to decrypt. You will need to decrypt the data package in order to access its content. - Once the data package is decrypted, you will gain access to information about network addresses and/or will be automatically credited DRK credits in your profile if that is the case. You can check your DRK credits balance at the Dark Market.
Decryption failed?
Try again. Things that influence in whether decryption of a file fails or succeeds:
- Decryption difficulty of a file (the higher the level of the Network and the higher the level of a node in this network from which the data package was downloaded, the higher the difficulty).
- Your CPU stats. If your CPU is not 100%, you are not using the full capacity of your decryption software. CPU stats affect executing of all software, including those used to decrypt files.
- Skill points of your decryption software, in skill Encryption and Data Analysis.
- If your Avatar has a boost in skill Encryption and Data Analysis
XP and Notoriety
How it Works: For every interaction with a network, players earn XP points. These points can be used to level up their characters.
Specific actions earn Notoriety points for players, which will then be translated in $NOR Runes.
Marketplace
Players will find items (software, virus cures, hardware, maintenance gadgets) that will enhance their performance in Dark City’s marketplace.
Players are also able to exchange DRK credits and put their own items acquired in game for sale in the market.